From leveraging bottlenecks to launching malware attacks, criminals are targeting the supply chain. Here's how to keep your freight—and information—safe.
How's this for scary? In the second quarter of 2021, cargo theft experienced a 253% increase by value, according to Sensitech's quarterly Cargo Theft Intelligence Report. The average loss per incident was $365,459.
Full truckload theft accounted for more than half of freight-related crime, in spite of its decrease from the first quarter of 2021, Sensitech's report finds. Pilfering—the practice of stealing select items out of a trailer—accounted for 44% of thefts and rose 10% during that period.
Electronics were the item du jour for thieves. Theft of computers, televisions, gaming consoles, and similar items rose 60% from the first quarter of 2021, and a distressing 92% since the second quarter of 2020. One incident alone involved an electronics load valued at $1.2 million.
RISKY BUSINESS
Moving freight in 2022 can be a tricky business. Not only are ongoing supply chain slowdowns generating opportunities for cargo thieves, but today's increased reliance on technology brings a whole new set of vulnerabilities with it.
It isn't just cargo theft that can keep U.S.-based shippers up at night, either. Instead, companies have to account for data breaches and malware.
"If your supply chain is reliant on technology, your data has to be that much more protected," explains Azad Ratzki, chief technology officer at BlueGrace Logistics, a third-party logistics provider in Riverview, Florida. "You get the benefits of efficiency, but if it goes down because of ransomware, what was once a purely physical process is now both physical and virtual."
The good news is that shippers can deploy strategies and technologies to ward off crime.
"With the enhancements that have been developed, such as geofencing, RFID, or electronic logging devices monitoring truck routes, there's better visibility than there ever has been before," says Eddie Leshin, senior advisor at BlueGrace Logistics. "Shippers can see where a product is in transit, whether it's on the right track, and whether it's being moved properly."
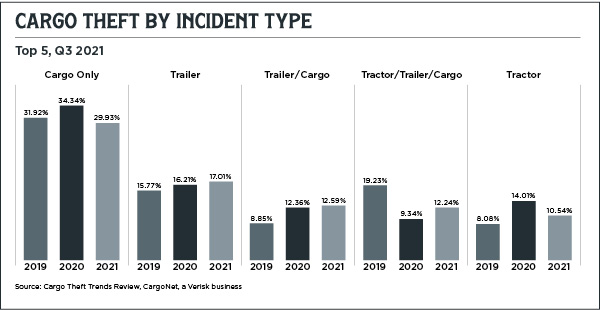
SLOWDOWNS MAKE FREIGHT A TARGET
Ongoing bottlenecks have made freight more vulnerable to attacks in transit. But numerous stops have always been an inevitable part of surface transportation, whether that's a driver stopping to take a shower or containers waiting at an intermodal yard. Unfortunately, that can make freight a prime target for thieves.
The problem worsened in 2020. In its annual Supply Chain Security Risk Report, CargoNet, a freight security consultancy in Jersey City, New Jersey, reported the first increase in cargo theft in years. Thanks to a combination of increased consumer demand and pandemic protocols, break-ins spiked from 1,104 instances in 2019 to 1,427 in 2020.
"Cargo thieves have never had a more favorable environment," the report notes.
"What jammed up the supply chain was the unprecedented pull of goods to the end user," says Keith Lewis, vice president of operations at CargoNet, a Verisk business. "We ended up with a shortage of truck drivers, a shortage of trucks, a shortage of trailers, and a shortage of container chassis. Add all that up and you get a lot of freight sitting for long periods."
By the end of 2020, those issues cost shippers $63 million in value, according to CargoNet statistics.
But carriers are not stuck waiting for a burglar to strike. They can use seals, locks, GPS systems, and telematics to ward off crime. Importantly, when it comes to security measures, there isn't a one-size-fits-all solution. Run a risk assessment and planning security measures in correspondence with the value of a shipment, recommends Bill Schoenherr, vice president at NovaVision, a security products company based in Bowling Green, Ohio.
"If you have a load to ship, don't do nothing," he says. "Even if your company is on a budget, get something as simple as a bolt seal.
"Depending on the type of shipment, you can layer multiple technologies, which we recommend as you do your risk assessment," he adds. "The main goal is getting the doors closed, locked up, and controlled."
It's just as important for carriers to have a plan with their drivers that goes beyond reminding them to park in a safe area. Backing up to a building and parking in well-lit areas are good starts, but Lewis recommends staying out of high crime areas altogether.
"Hot spots or danger zones are all over the United States," he says. "If my drivers will run out of hours and finish the day in a high theft area, I tell them to stop a half hour earlier in the middle of nowhere. That greatly reduces the risk of theft."
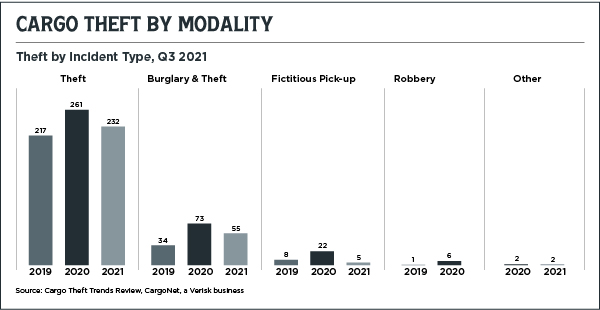
SECURING WAREHOUSE INVENTORY
Cargo security is equally important once freight reaches its (temporary) destination. Warehouses can be compromised in a few different ways.
For one, employee churn is notoriously high. In 2018, turnover averaged 32.5% among warehouse employees, according to a 2019 International Association of Refrigerated Warehouses survey. This can leave warehouses vulnerable to bad actors.
But attacks can obviously come from the outside as well. In November 2021, three men were indicted following a failed warehouse heist outside of Long Beach, New York. The trio allegedly broke into the warehouse wearing fake police tactical gear, restrained employees, and stole inventory worth hundreds of thousands of dollars.
"In today's environment, we deal with a lot of unique situations," says James Spence, principal consultant at ADT Commercial. "Computer chips, for example, are now at an extremely high value. You have to put an extra level of protection around any logistical environment that houses items like computer chips."
As a result, warehouses perform security audits and use tools like access credentials, Bluetooth door readers, intrusion detection, and license plate readers to unlock a gate.
"For warehouses that see high turnover or store high-priced inventory, it's best to avoid manual processes," says Bernhard Mehl, CEO and co-founder of KISI, a physical security system provider in New York City. "You can set up a system to decide which groups of people have what level of access."
USING DATA TO FIND WEAK SPOTS
A big benefit of utilizing the available technology is collecting data. A few weeks or months of surveillance information can be helpful for identifying security weak spots.
"If a security breach or theft happens, you can go back and investigate the data that you've collected," says Mehl.
VIRTUAL THREATS ON THE RISE
In addition to physical security, threats are becoming increasingly common in the virtual world. Cybersecurity breaches are on the rise, and logistics firms are not an exception to that trend.
Cybercriminals use malware and bots to exploit security weak spots and gain access to a company's confidential data. In addition to financial harm, cyberattacks can compromise the security of any vendor or partner that a firm works with.
"As long as a company has information that is valuable to hackers, they will be a target," notes Pierluigi Stella, chief technology officer of Network Box, a cybersecurity service provider in Houston, Texas. "Sometimes a logistics firm isn't even the target, but hackers use it as a vehicle to target somebody else."
These attacks are often facilitated through email phishing scams. Hackers gain access to company information when an employee accidentally downloads malware through an email attachment or link.
Many attacks involve ransomware, where cybercriminals encrypt sensitive data and then demand payment (a ransom) for its return. Companies on the receiving end of this extortion may even find that a hacker has sold their information on the internet. Ransomware incidents rose by 715% in 2020, finds a BitDefender report.
But even truck equipment can potentially be hacked. In June 2020, the FBI circulated an advisory warning that cybercriminals could breach electronic logging devices to access company networks or gain control of the truck engine itself.
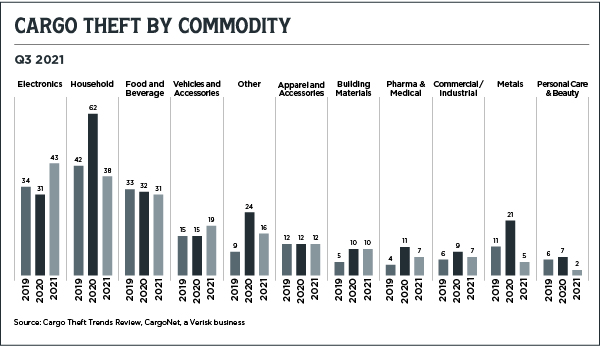
CYBERSECURITY FROM THE TOP DOWN
These types of attacks can be mitigated through company-wide awareness, starting from the top down.
"Cybersecurity needs to be a boardroom conversation that is addressed on day one," says Vijaya Rao, founder and CEO of Techvio, an IT solutions platform in Philadelphia. "Companies need to take a 30,000-foot view and decide what their cybersecurity goals are.
"If you have a security operations protocol determining how data is handled within the company, decide what protections are needed, and who has access to what," he adds. "That is how you maintain a strong cybersecurity posture."
Firms don't have to be sitting ducks, waiting for an attack to happen. "Some small or mid-sized businesses might be reluctant to invest in these measures," says Ratzki. "But business owners can feel good knowing that their company is protected."